-
Our offeringsDigital Risk ProtectionEmergency Response ServicesCyber Threat IntelligenceSpecialized ServicesFeatured News

CSIS has achieved CREST accreditation for incident response, validating our expertise and commitment to the highest cybersecurity standards.
- Your challenges
- Resources
-
About us
- Cyberhagen
- Careers
-
-
Digital Risk Protection
-
Emergency Response Services
-
Cyber Threat Intelligence
-
Specialized Services
-
About us
AD SECURITY ASSESSMENT

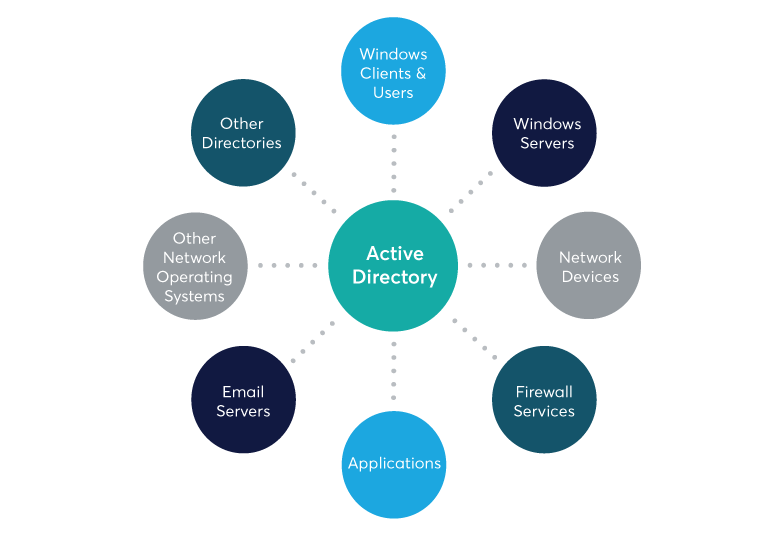
Active Directory (AD) is a crucial part of an organization’s network
AD is the lifeblood of modern networks, and without it, the whole organization can grind to a halt.
Attackers target the system to access and obtain new credentials to help them move laterally in the network.
Its progressive nature and the complex security framework gives an unfair advantage to attackers.
Based on observations made during incident response assignments and penetration test assignments, we can confirm that the IT criminals put significant effort towards attacking Active Directory.
If an attacker gains access to your AD, they control your organization

Don’t take any chances.
Have your AD assessed.
ESSENTIAL CHECK
25 essential controls to see if the Active Directory follows the most widely accepted best practices and ensures that attackers cannot obtain access with most used attack tools.
Examples of controls:
- Credential stealing and account takeover
- Misconfiguration of privileged users
- Kerberoasting of privileged users
- Hardening of Enterprise, Domain and Local Administrators
- Access Control List misconfigurations
- Strong password policies
- Best practice audit logging
- Domain & forest functional levels
EXTENDED CHECK
A further 75 controls gives you a more in-depth analysis and better coverage of your security posture. The result leaves you with a healthy level of security that can withstand even skilled attackers.
Examples of additional controls:
- Protections against advanced credential-stealing attacks
- Unconstrained delegation analysis
- Protections against Golden and Silver Ticket attacks
- Legacy protocols and broken cryptography primitives
- Implanted malicious accounts and Shadow Administrator activity
- Analyzing group policies for credential leaks
- Best practices in architecture such as Administrative Tier Model and Enhanced Security Administrative Environment (ESAE)
- Control path analysis
Our methodology is
extensive & fast
CHRONOS
We leverage our proprietary, purpose-built platform to ensure a fast, accurate, and effective service delivery process.
- Scales, automates and improves every aspect of the investigative process, from data collection, to analysis and reporting.
- It takes only 5 minutes to run our application and it can be run from anywhere.
- Powerful intelligence and analytics tools ensure depth and breadth of analysis.

Request a call
Rest Assured.
We are the leader in actionable and intelligence-driven detection and response services.
