-
Our offeringsDigital Risk ProtectionEmergency Response ServicesCyber Threat IntelligenceSpecialized ServicesFeatured News

CSIS has achieved CREST accreditation for incident response, validating our expertise and commitment to the highest cybersecurity standards.
- Your challenges
- Resources
-
About us
- Cyberhagen
- Careers
-
-
Digital Risk Protection
-
Emergency Response Services
-
Cyber Threat Intelligence
-
Specialized Services
-
About us
COMPROMISE ASSESSMENT SERVICES
Our Compromise Assessments are an essential business need for all organizations
Increasingly, companies around the world understand that Compromise Assessments are a basic business imperative as they enable them to:

Undertake compromise assessment
At the same time, companies understand that a ‘prevention’ strategy alone does not work. The worrying reality is that it often takes companies over 100 days to discover that they have been breached. It is during this time that criminals do more and more damage.
A crucial step toward having a strong security posture is undertaking Compromise Assessments.
This is because Compromise Assessments with CSIS are a proactive and in-depth look at your full network, at an endpoint level, through which we deliver a comprehensive and interconnected set of technical assessments:
- Threat Assessment: Are there any indications of threats (malicious actors) present on my network?
- Risk Assessment: What risks is my network exposed to that could pave the way for malicious actors to gain access?
- Windows Security Assessment: Which Operating System-level security settings are out of line with best practices and, therefore, represent a threat vector?
Features
Benefits
We deliver results. Fast.
Most Compromise Assessment engagements will last <4 weeks. Even for large-scale assignments. We follow a standard 3-step methodology, which is both non-invasive and non-disruptive.
OBJECTIVES:
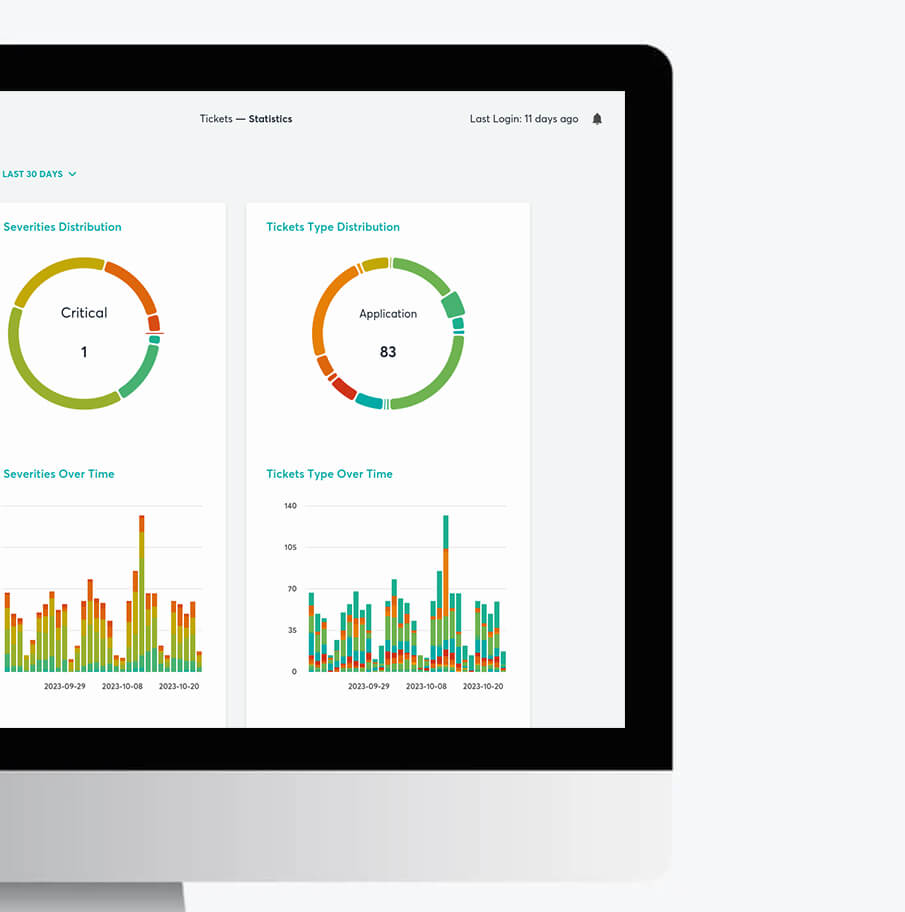
Delivered by expert consultants
POWERED BY WORLD-CLASS TECHNOLOGY
Our industry-leading service is supported by “Chronos”, the world’s most powerful cybersecurity investigations platform. Chronos allows us to assess your entire network accurately, without sacrificing depth or speed, while avoiding bank-breaking fees.
- Scales, automates and improves every stage of the investigative process, from data collection, to analysis and reporting.
- It takes minutes to run our application.
- Powerful intelligence and analytics tools ensure depth and breadth of insights.
Rest assured
No matter what the findings, a Compromise Assessment is beneficial because you will either:
- Gain peace of mind should the assessment show that there are no threats or risks present in your network, or
- Be able to initiate a series of well-defined actions to mitigate the consequences of a threat or risk, before it becomes a full-blown incident.
Request a call
Rest Assured.
We are the leader in actionable and intelligence-driven detection and response services.
