-
Our offerings
.png?width=538&height=522&name=5%201%20(1).png) Digital Risk Protection
Digital Risk ProtectionWorld-class threat intelligence to protect your organization and your customers.
ConsultingHighly specialized services to identify and remediate complex risks and threats.
Emergency Response ServicesGet a fast response from world-class experts and rapidly reinstate business continuity.
Cyber Threat IntelligenceWord-class data, analysis and insights on threat actors and the evolving threat landscape.
SPECIALIZED SERVICESWe offer specialized services to address our customers' specific requirements that have been brought about by specific market developments and trends.
- Your challenges
- Resources
-
About us
- Careers
-
-
Digital Risk Protection
World-class threat intelligence to protect your organization and your customers.
-
Consulting
Highly specialized services to identify and remediate complex risks and threats.
-
Emergency Response Services
Get a fast response from world-class experts and rapidly reinstate business continuity.
-
Cyber Threat Intelligence
Word-class data, analysis and insights on threat actors and the evolving threat landscape.
-
SPECIALIZED SERVICES
We offer specialized services to address our customers' specific requirements that have been brought about by specific market developments and trends.
-
About us
EMERGENCY RESPONSE

Sooner or later a breach will happen
-
Digitalization is pervasive.
-
Attacks surfaces are growing.
-
Cyber criminal don't rest.
74
%
of small businesses had a security breach. Up to 60% from one year before
Our team is second to none
We are the first port of call for leading companies across all sectors and we have amassed incomparable experience by working on many of the largest and most complex incidents. These are the types of incidents we help companies resolve:
Getting the right insights
Our Emergency Response Consultants have all got significant experience from having worked on enterprise-scale incidents.
As a tight-knit team, they work unrelentingly with our customers to ensure the answers to four key questions are discovered:
A tried and tested process
Our Emergency Response process is based on the SANS Institute model, though adapted based on our experience. The high-level process flow follows four steps:
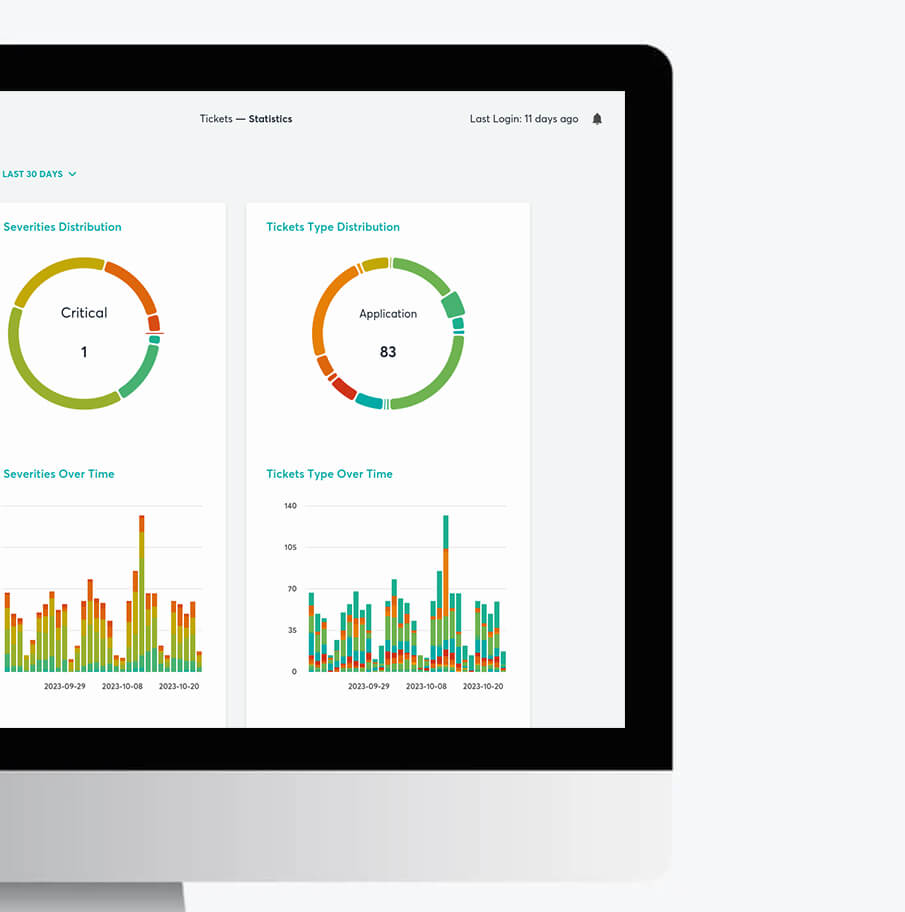
Our proprietary tech
CHRONOS
A fully-fledged emergency response platform that has been optimized for medium and large-scale incidents that require a rapid and detailed investigation and complex situations where the precise nature and scale of an incident are not necessarily known.
CIRK
A powerful remote forensics tool that is ideal for small-scale incidents that require investigation into computers that are known to be infected.

Our experience is our key differentiator
No two incidents are the same
We do not apply cookie-cutter consulting methodologies. Our approach is a guideline. We let the evidence lead us to conclusions.
We assign people with depth and breadth of expertise
You will be led and supported by experts, each of which has amassed significant experience having been at the coalface of numerous incidents.
We understand the importance of being cost-effective even when delivering the highest quality
Incidents can be extremely costly when all is said and done. We are sensitive to this and have optimized our approach to maximally leverage remote intervention. Our tools facilitate this process.
“CSIS brought rigor, creativity, persistence and excellence to the table. Thanks to their invaluable work, we were able to resolve a critical cyber incident. Beyond the investigation and tactical support, we have been able to leverage expert advisory services to define and implement critical improvements. We recommend their services to any company that wants to become more cyber resilient.”

Companies that have worked with us understand the relevance of taking out an Emergency Response Retainers with us. Retainers provide significant benefits, including priority access to our Consultants.
Request a call
Rest Assured.
We are the leader in actionable and intelligence-driven detection and response services.