Credential Misuse & Identity Theft
Credential Misuse and Identity-Based Attack Vectors
Dénes Olivér Óvári, Detection and Response Architect
Gustav Stofberg, Principal Security Consultant
CSIS Security Group A/S
From Credentials to Identity
At the beginning of their guidelines [1], NIST defines (digital) identity as the online persona of a subject and notes that a single definition of digital identity hasn’t been widely agreed on so far. However, for our purposes this definition is satisfactory. We take it as a “digital identity represents a subject in an online transaction”.
Digital infrastructure access traditionally relies on data associated with such an identity [2]. That is, to gain access to a digital service, the subject must know a “secret”, in other words: a credential.
The identity of the subject is then assumed by the system based on their knowledge of a password, a PIN, an API key etc. Therefore, in this case the theft of a credential equals identity theft.
Reliably proving a subject’s true identity relies on combining more factors:
- Something they know – in the example above, the “secret”.
- Something they have, for example a trusted platform module (TPM), a security token etc.
- Something they are, such as biometric data.
Credential Misuse on the Rise
According to the 2023 Data Breach Investigations Report [3] in the analysed timeframe covering most of 2022, 49% of all breaches involved credentials. Moreover 74% of breaches included the human element, which is often related to identity-based attacks.
The tendency seen in Microsoft’s Digital Defense Report 2023 is chilling [4]. The number of password-based attacks observed in April is ten times the number seen in the same month a year before!
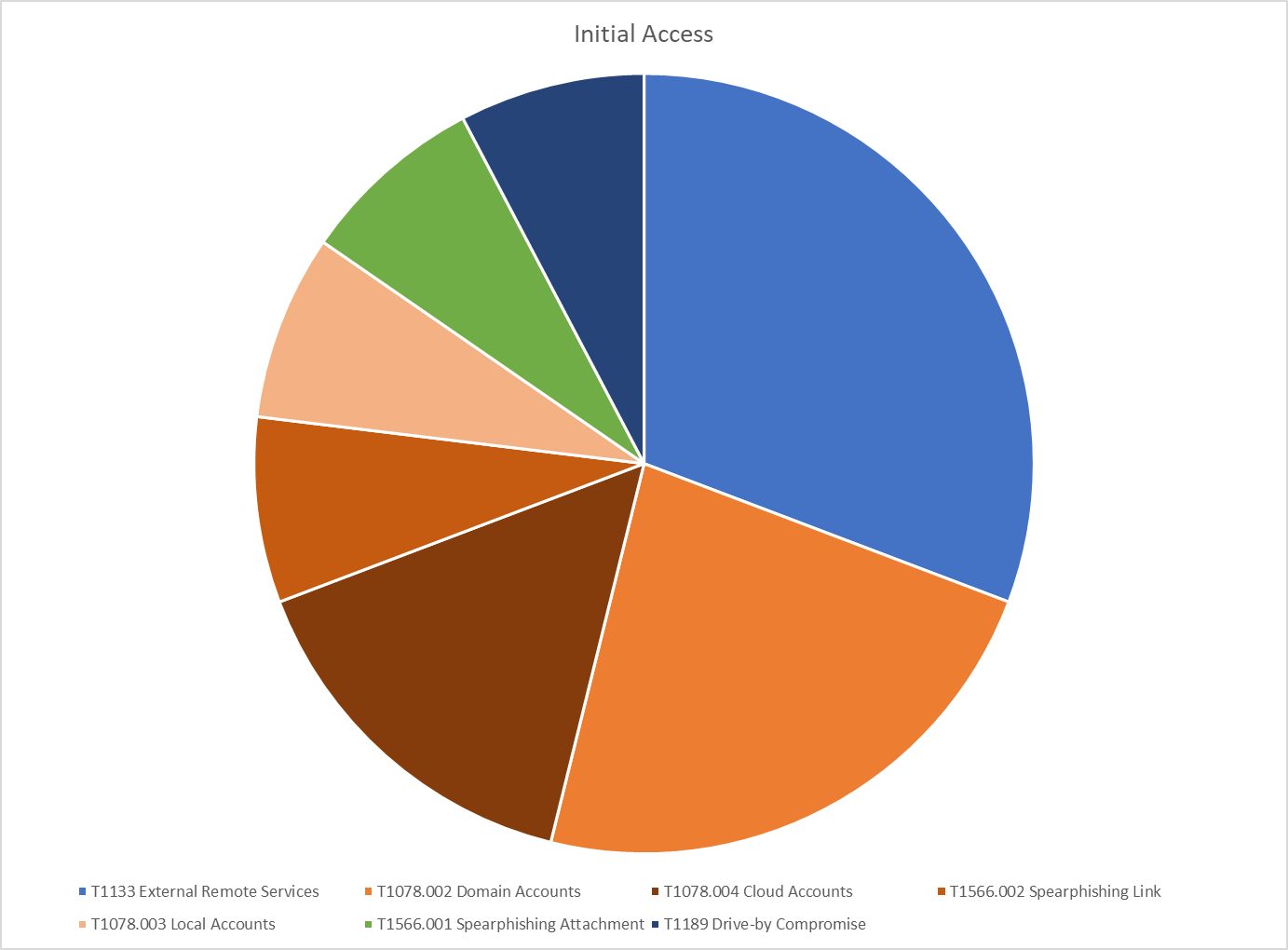 Figure 1: Initial Access tactics observed during incidents handled by CSIS in H1 2023
Figure 1: Initial Access tactics observed during incidents handled by CSIS in H1 2023
Our own statistics for this year so far are in line with the trends seen in the two reports referenced above. Figure 1 shows that in 46% of the cyber incidents we dealt with in the first half of 2023, we observed sub-techniques of the T1078 Valid Accounts technique of MITRE ATT&CK® being used during the Initial Access phase. This technique covers all usual types of credential abuse adversaries might employ.
Bypassing MFA?
Multi-factor authentication will deny access to the system unless all the required factors are provided, deeming that the subject’s identity is impossible to ascertain. For instance, a common MFA implementation requires the user to enter a One Time Password (OTP) received in an SMS, in addition to their username & password pair.
Nevertheless, while combining more factors does increase security, the system could still be insecurely configured. Vulnerabilities may exist in software or hardware too. An example is a recent incident we worked on, where the perpetrator successfully carried out a real-time spear phishing attack against a customer, even though the customer’s infrastructure did enforce MFA.
The attack started with an email. An employee received a message containing obfuscated links ultimately redirecting the user’s browser to a bogus site set up by the adversary. The site mimicked the genuine Office 365 login page, down to replicating even the customer’s own branding.
The unsuspecting user entered their credentials on the phishing site, followed by the OTP required by the multi-factor authentication as well. Due to configuration flaws [5] though, the perpetrator could steal and misuse a valid security token through the fake login site. This token allowed them to entirely bypass MFA, leading to a data compromise.
We strongly recommend establishing a phishing-resistant multifactor policy, incorporating security devices like YubiKey or similar. Implementing such measures not only enhances protection, but also makes it impossible to fall victim to malicious activities such as session stealing.
Recommendations
- Implementing proper Access Control
- Monitoring the infrastructure - audit logs!
- Develop and maintain a cyber incident response plan [6]
- Have an Emergency Response partner at hand.
Thanks to our colleague, Conor Kelly for his review.
“Microsoft, Office 365 are trademarks of the Microsoft group of companies.”
References
| [1] | NIST Special Publication 800-63 Digital Identity Guidelines, 2017. |
| [2] | Ev Kontsevoy, Sakshyam Shah, and Peter Conrad: Identity-Native Infrastructure Access Management, O’Reilly Media, Inc., 2023. |
| [3] | The Verizon DBIR Team: 2023 Data Breach Investigations Report, 2023. |
| [4] | Microsoft Digital Defense Report 2023 |
| [5] | Microsoft Security Experts: Token tactics: How to prevent, detect, and respond to cloud token theft, 2022. |
| [6] | FEMA: Planning Considerations for Cyber Incidents, 2023. |

.jpg?width=500&height=566&name=Bech%20Bruun%20CSIS%20signing%20contract%20(1).jpg)

