-
Our offeringsDigital Risk ProtectionEmergency Response ServicesCyber Threat IntelligenceSpecialized ServicesFeatured News

Our Latest Threat Matrix Report Is Out! Where we break down the latest threat developments and share what organisations should be preparing for in 2026.
- Your challenges
- Resources
-
About us
- Cyberhagen
- Careers
-
-
Digital Risk Protection
-
Emergency Response Services
-
Cyber Threat Intelligence
-
Specialized Services
-
About us
THREAT MONITORS

Organizations need
high-quality
digital risk protection to be resilient
The CSIS Threat Intelligence Services team is highly skilled and able to monitor and track threat actor activities, investigate command and control servers, recover and reverse phishing kits and panels, and recover credentials and leaked data from drop sites.
We provide organizations with complete coverage using a wealth of aggregated data from underground marketplaces, research activities, incident response learnings, and other private and public sources. This ensures that organizations can rest assured, knowing that they are fully protected against potential security threats.

Threat monitors delivering unique data
Payment Cards: stolen, leaked, and compromised payment card information from data from sources on the darkweb, underground marketplaces, and data recovered from phishing sites.
Customer and Employee credentials: compromised credentials related directly to your customer-base or employees.
Telegram monitoring: mentions of your brand or specific keywords in Telegram closed chats and communities.
HoneyNet monitor: we monitor a vast number of malicious servers and domains all over the world and analyze sinkholes for any communication from your public IP ranges
Trojan Monitor: we monitor Trojan target lists and config files for your URLs and brands, and if you are targeted (or if a specific Trojan threat arises in your region), you will be the first to know.
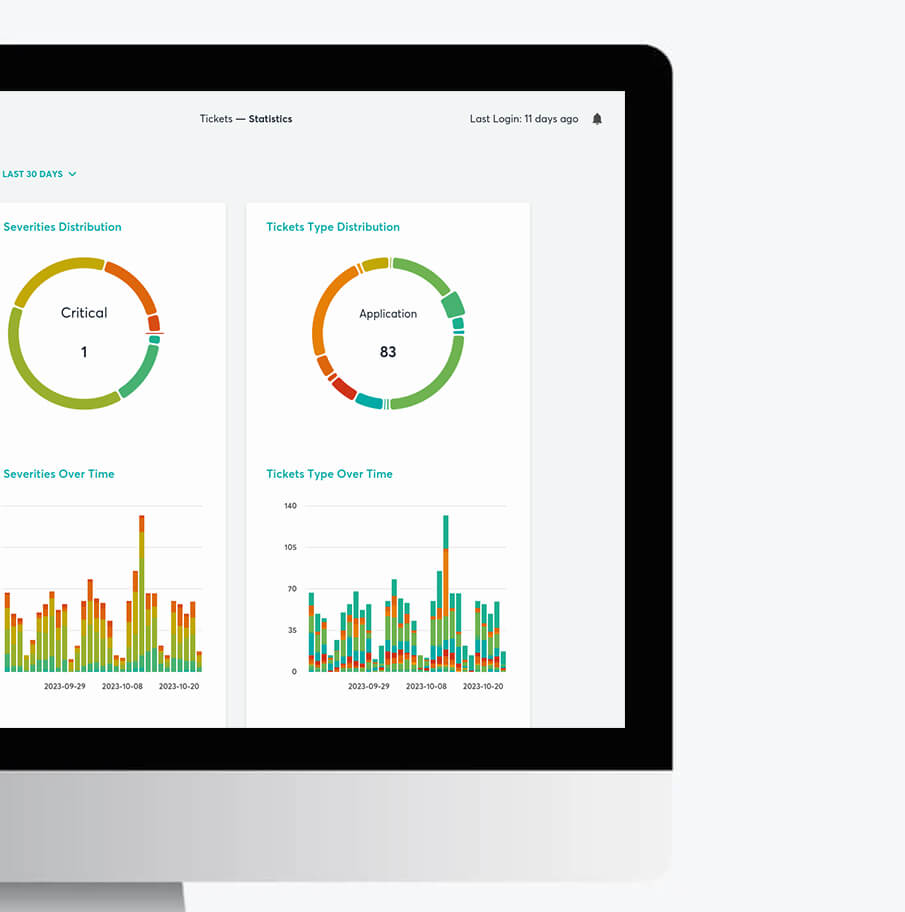
24/7 real-time monitoring
Threat Monitoring service is a cybersecurity solution that is designed to keep a close eye on any potential security breaches. Get notified immediately in the event of data leaks, stolen credentials, or mentions of certain keywords on Telegram communities or the dark web.
Benefits.
Request a demo
Rest Assured.
We are the leader in actionable and intelligence-driven detection and response services.
